
When you connect to a web site using SSLhttp://www.windowsecurity.com/articles/Secure_Socket_Layer.html,your browser asks the server to authenticate itself, or confirm its identity. The authentication process uses cryptography to verify that a trusted independent third party, or certificate authority, such as Thawte or VeriSign, has registered and identified the server. SSL can also authenticate connecting users or their computers.SSL encrypts the data that you send, and incorporates a mechanism for detecting any alteration in transit, so that eavesdropping on or tampering with web traffic is almost impossible. This is essential for safely transmitting highly confidential information such as credit card numbers

When I clicked "My MSN", the homepage can be personalized(it is like igoogle personalized homepage).
For"MSN money", it is also not very attractive. Yahoo finance and google finance should be more reliable information resources due to the reputation.
For"msn People & Chat"

Hotmail space is 1G, it is much smaller than Yahoo's current 3.5G and unlimited in the near future.But hotmail gave me a good interface, it does not make me feel the mail box is like full of junk and advertisement, the main contents show well.
Once the Hotmail security had flaw exposed http://seclists.org/fulldisclosure/2005/Jun/0018.htmland we can not say there is no available expoilts for hotmail, but microsoft is a respectable company and you just need to make you updated with the security issues, generally it will make you safe to use the service they provide. When you sign in to MSN Hotmail, your sign-in name and password are encrypted and then sent over the Internet using an SSL connection. No one can read or access the data that is being transmitted.After you sign in and leave the encrypted connection, MSN Hotmail keeps track of who you are by using a computer-generated key rather than your Hotmail sign-in name. MSN Hotmail regularly refreshes this key to make it difficult for anyone else to pose as you. For current email users, spam is a lot of anoyance except that wastes the user's time, some spams contain virus and do some phishing work to try to solicit the user's personal information to exploit it to benefit the spam author.
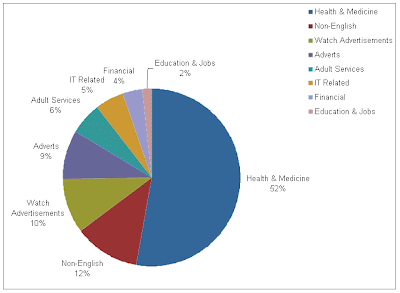 The ways to deal with anti-spam:
The ways to deal with anti-spam:
1.Be careful about sharing your email or instant address
2.ignore spam
The details can be looked up at http://www.securityfocus.com/infocus/1763
Current anti-spam solutions fall into four primary categories: filters, reverse lookups, challenges, and cryptography. Each of these solutions offers some relief to the spam problem.
For hotmail users, you need remember the above two tips and update your hotmail security service if the updates are available and make full use of anti-spam function of the mail.By the way, I do not like the currently available windows live mail beta even the space has increased to 2G, it is not convenient for me to pick up the right contacts when I tried to send the email. Maybe wait after the version is not beta.












 Actually, the current network security is still evolutionary, the gateway becomes more complex, the anti-virus and operating systems becoming more and more complex, but if some dramatical virus appears, it will crash millions of systems, that kind of scenarios have happened again and again.
Actually, the current network security is still evolutionary, the gateway becomes more complex, the anti-virus and operating systems becoming more and more complex, but if some dramatical virus appears, it will crash millions of systems, that kind of scenarios have happened again and again.




 Technology with law can crack down the computer crimes finally, I think.
Technology with law can crack down the computer crimes finally, I think.
 In those days, crptography is far away from the routine life of the ordinary people, it is generally used between the countries or between the leaders of two tribes, they need to exchange the information to unite to fight for the intrusion or something urgent.The algorithm used those days is so simple from today's view, for example caesar cypher
In those days, crptography is far away from the routine life of the ordinary people, it is generally used between the countries or between the leaders of two tribes, they need to exchange the information to unite to fight for the intrusion or something urgent.The algorithm used those days is so simple from today's view, for example caesar cypher

